Can Hackers Really Clone Your Keys, Intercept Your Fobs, or Replay Your Garage Remote?
Yes, and it happens faster than you think.
Most people carry their keys like it’s 1999: visible, noisy, and dangerously easy to clone. In 2019, Consumer Reports found that some cars could be unlocked and started using relay attacks in under 30 seconds. That remote clipped to your visor may not be broadcasting all the time, but it’s still vulnerable to replay attacks, and it’s easy pickings for a thief to grab.
Ethical hacker Ryan Montgomery, known as @0day, is showing millions just how exposed everyday keychains really are. This post breaks down the risks attackers already exploit and how Keyport helps you carry smarter.
Quick Answer: Can Your Keychain Be Hacked? Here’s How to Protect Your Keys from Hackers
Yes. Your keys, fobs, and garage remotes can all be hacked. Cloned. Intercepted. Replayed. If you’re carrying them out in the open, you’re making it easy.
Keyport's helps you carry smarter with a secure, modular, and low-profile EDC system. Our key organizers are built for both security and style, concealing your vulnerabilities and reducing your exposure.
Why Trust Us
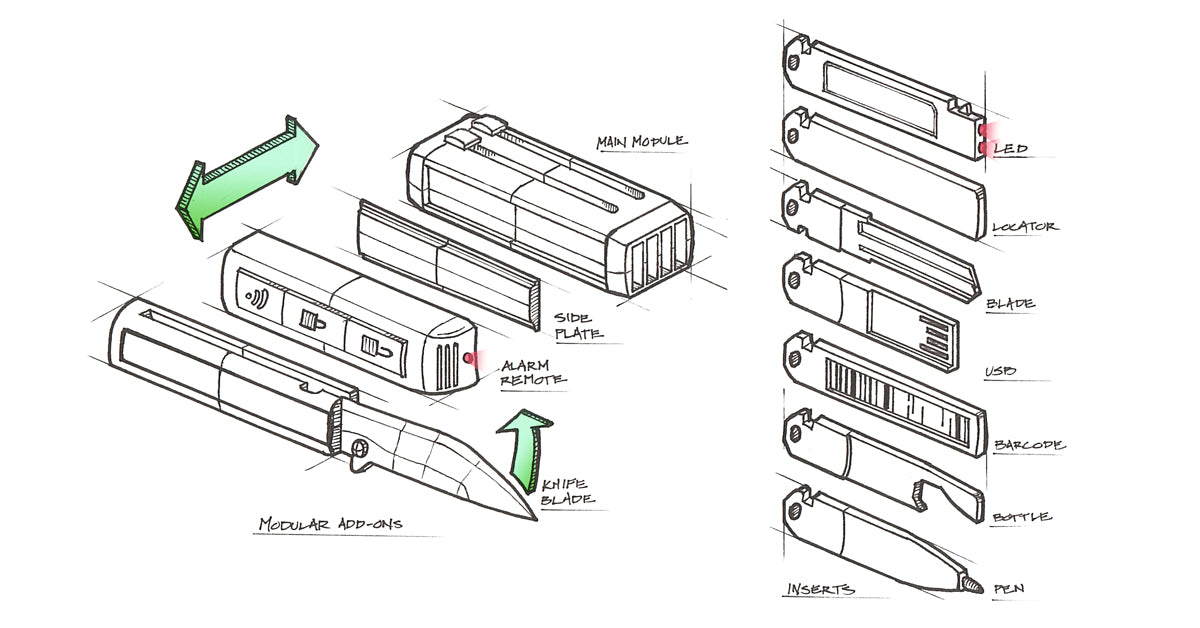
Keyport pioneered the modular everyday carry system nearly a decade ago. Our products secure your keys, fobs, tools, and identity in a single, customizable setup built for real-world use. With thousands of customers and a reputation for thoughtful design, we're here to help you carry smarter, not louder.

Key Takeaways: What Ryan Montgomery Exposes, Keyport Helps You Secure
Ryan Montgomery exposes how everyday carry mistakes can make you a target.
Key photos, RFID fobs, and garage remotes are easier to compromise than you think.
Keyport conceals keys, controls fobs, and improves your EDC security.
Features like KeyportID and accessories the KO Pocket Clip and KO Magnetic Quick Release reduce risk and loss.
Keyport helps you carry smarter without sacrificing style, weight, or accessibility.
Table of contents
How Hackers Exploit Keychains, Fobs, and Garage Remotes
That bulky, jangling mass of keys on your hip? It’s more than annoying. It’s a vulnerability.
- Visible key blades can be photographed and duplicated using just a smartphone
- RFID fobs and NFC badges can be scanned without your knowledge, making them vulnerable to stealth cloning attacks.
- Garage remotes with fixed codes can be intercepted and replayed with cheap devices
- Dangling keys are easier to steal, pickpocket, or track from a distance
Imagine you're at a coffee shop. Your keys are sitting on the table. Someone across the room takes a photo. By the time you finish your latte, they've uploaded the image, generated a CAD model of your key, and 3D-printed a copy. Your front door is now one step closer to being compromised - with oat milk.
In 2008, UC San Diego researchers demonstrated that keys could be duplicated from a photograph taken from over 200 feet away. Today's phone cameras are even better.
Most people carry their keys in ways that unintentionally help attackers. Exposed keys, noisy keychains, and visible fobs all create openings that are easy to exploit.
Ryan Montgomery Exposes the Vulnerabilities
Hacker and cybersecurity expert Ryan Montgomery has gone viral for exposing how everyday keychains, fobs, and remotes leave you wide open. He is not trying to scare you (although it is pretty unsettling), he does it so you’re no longer an easy target.
Here are five of his most revealing videos, and what they demonstrate:
In this rapid demo, Ryan Montgomery (aka 0DayCTF on YouTube and TikTok) uses a Flipper Zero running the Key Copier app to scan a Kwikset KW1 key. By aligning the key with the Flipper’s onboard optical sensor, he extracts the key’s bitting pattern—essentially its digital fingerprint.
While the Flipper can’t cut keys itself, the bitting data can be given to any locksmith or entered into key duplication software to create a perfect clone.
Key insight: You don’t need a key cutting machine to duplicate someone’s key—just a moment to scan it and access to a locksmith later.
Why it matters: If someone gets near your keys, they don’t need to steal them. They only need seconds to capture the data that opens your front door.
In this short demo, Ryan Montgomery uses a Flipper Zero to scan a standard 125kHz RFID key fob—commonly used for apartment buildings, pools, and offices. These low-frequency fobs typically don’t use encryption, which makes them especially vulnerable to cloning.
After capturing the fob’s unique ID, Ryan writes that data to a blank RFID tag, effectively creating a duplicate. He then uses the cloned fob to unlock the door - no cracking or brute force required. It's consumer-available tech that happens to be surprisingly powerful and a few seconds of proximity.
Key insight: Many common RFID systems rely solely on unencrypted IDs. If someone gets near your fob, they can clone it and walk through the same doors you can.
Why it matters: If your fob can be copied this easily, your security depends entirely on whether someone wants to exploit it.
In this clip, Ryan Montgomery uses a Flipper Zero to demonstrate a signal capture and replay attack against a car’s key fob system. When the fob button is pressed to lock or unlock the car, the Flipper records that signal and then replays it later to unlock the car without the key.
This works because many cars still rely on fixed codes or weak rolling codes, making them vulnerable to replay-style breaches. The Flipper Zero is a consumer-available hacking tool that costs under $200 and fits in your pocket. No special access or advanced skill required - just proximity and timing.
And this isn’t theoretical.
In 2018, researchers showed that Tesla Model S key fobs could be cloned using a $600 Proxmark radio tool by breaking their encryption. The attack allowed thieves to unlock and start the car in seconds. Since then, Tesla and other automakers have improved their systems, but plenty of older vehicles remain exposed.
Montgomery’s Flipper demo shows that vulnerabilities in keyless entry are still very real, and disturbingly easy to exploit.
Ryan Montgomery explains that many garage door systems still use static codes, meaning they send the same signal every time the button is pressed—making them easy to record and replay with simple radio tools like the Flipper Zero.
Even newer “rolling code” systems, which are designed to change the code each time, are not immune. Some of these protocols have been broken, allowing attackers to capture and replay a valid code to open the door later.
At DEF CON 23, security researcher Samy Kamkar demonstrated a $30 device called RollJam that could intercept and replay garage remote signals - even those with rolling codes.
Ryan's advice: While upgrading your opener is ideal, most people forget the critical step of locking the interior door between the garage and the home. A closed garage isn’t enough. One unlocked door is all it takes to turn a replay attack into a full breach.
In this demo, Ryan Montgomery shows just how quickly a hacker can skim a key fob from someone walking by. With a simple tap using a handheld RFID reader, he captures the fob’s data without the person ever noticing. Seconds later, he emulates the fob to gain access to a restricted building. It’s a vivid, high-speed demo that drives home one truth: convenience in lock tech often means weak physical security.
The lesson: If your fob isn’t shielded, it’s vulnerable. Ryan recommends using an RFID-blocking sleeve to keep your access credentials from being silently stolen on the go.
Who Is Ryan Montgomery?
Ryan Montgomery is an ethical hacker and cybersecurity creator with millions of followers on TikTok and YouTube. Known online as @0day, he exposes real-world vulnerabilities in the devices people use every day - from garage door openers to key fobs to smart locks. His goal? Making the digital and physical world harder to exploit by raising awareness and promoting smarter, safer habits. While Ryan is not affiliated with Keyport, we respect his work and share the same mission.
Ryan also serves as Chief Ethical Hacker for the Sentinel Foundation, a nonprofit that works with law enforcement to expose online predators and stop child exploitation. His ability to channel technical skill into real-world impact is something we deeply admire.

Common Keychain Mistakes Hackers Look For
The noisier and bulkier your keychain, the more attention it draws, especially the kind you don’t want. Hackers and thieves aren’t just opportunists anymore; they’re observers looking for visible access points you didn’t realize you were advertising.
Here's what raises red flags:
Keys dangling from belt loops - Easy to spot, easy to photograph, and even easier to swipe in a crowd
Keychains with 10+ visible tools and keys - Tactical-looking doesn't mean secure; it often signals "steal me"
Exposed RFID fobs - Vulnerable to digital skimming and signal cloning if left unsecured
Garage remotes clipped to visors - Can be intercepted with signal replayers or stolen directly from the car
Bulky multitools and carabiners - Advertise that you’re carrying gear worth grabbing
Carrying smart doesn't mean carrying less; it means carrying better.
How Keyport Helps You Carry Smarter and Safer

You don’t need to sound like a walking toolbox to carry your essentials. Traditional keychains jangle, dangle, and advertise vulnerabilities. Keyport is built to reduce that exposure without adding bulk or sacrificing style.
Here's how:
🔐 Conceals Key Blades – Keys are stored inside the Pivot 2.0 or Slide 4.0, not dangling out where anyone can photograph and clone them.
🛰️ Reduces Signal Exposure – Traditional RFID fobs can be duplicated onto smaller, thinner RFID keys via our partner CloneMyKey, allowing them to fit discreetly inside your Pivot. NFC tools like our Popl x Keyport Digital Business Card can be carried the same way. The Pivot's metal chassis act as a passive signal barrier like a faraday cage.
🧠 KeyportID Lost & Found – Our anonymous recovery service helps return lost Keyports without revealing name or address. No batteries, no Bluetooth, no tracking.
🔧 Modular Attachments – Use the KO Pocket Clip to carry your setup fully inside your pocket. Only the clip shows - nothing jingles or dangles.
💡 Pocket Flare 2.0 – Adds a compact light module to your carry - no more fumbling with your phone in dark garages or stairwells.
How to Secure Your Garage Remote and Car Fob
Most garage remotes are clunky relics from the ’90s, and people still clip them to their sun visor like it’s perfectly normal. It’s not.
Remote signal replay attacks are real. And they work frighteningly well. A thief can capture your remote’s signal, then reuse it to open your garage when you’re not around. Even newer rolling code systems have known exploits.
While you can’t stuff a chunky garage clicker into a Keyport housing, the way you carry it still matters.
Here’s how Keyport helps:
Use a KO Magnetic Quick Release to detach your fob easily and store it in a safe pocket
Stop leaving your garage and gates remotes in the car or at least hide them. A visible garage or gate remote is an open invitation. Thieves know exactly what it is and what it unlocks.
Build better carry habits. Keyport’s modular system makes it easy to build an intentional, secure EDC setup.
Smart carry isn’t about paranoia. It’s about keeping your access out of sight and out of reach.
Modular EDC = Modern Security
There’s a reason security pros, operators, and urban minimalists are moving on from bulky keychains. Not because they want to look cool (although a Keyport does that), but because they want control.
Modular EDC gives you options:
Carry only what you actually use
Conceal keys, fobs, and tools from prying eyes
Customize for setup for specific environments (urban, travel, tactical)
Swap modules without rebuilding from scratch
The best gear stays out of the way until you need it. That’s the Keyport difference.
🔐 Key Take: Ryan exposes the vulnerabilities. Keyport helps reduce your exposure.
Traditional Keychains vs. Keyport (Comparison Table)
Feature |
Traditional Keychain |
Keyport Modular System |
|---|---|---|
| Key Blade Exposure | Visible & clonable | Hidden inside Pivot/Slide |
| Fob Security | Exposed & broadcasting | Concealed or detachable |
| Remote Control | Dangling or on visor | Clipped & stored when not needed |
| Pocket Profile | Bulky & noisy | Slim, silent, modular |
| Lost & Found | Tag with personal info | Anonymous recovery ID |
| Style Factor | Clunky and outdated | Sleek and customizable |
Final Verdict: Your Keychain Is a Security Risk - Here’s How to Fix It
Most people carry their keys, fobs, and remotes in ways that broadcast access to their life. Ryan Montgomery is pulling back the curtain on just how easy that is to exploit. But awareness is power. You don’t have to carry like a target.
Keyport offers a smarter way. Modular. Concealed. Purpose-built. It reduces your exposure without adding bulk or sacrificing convenience. It’s not just better design; it’s operational security for your pocket. In a world where your keychain can be hacked, Keyport makes your everyday carry smarter, safer, and harder to compromise.
Frequently Asked Questions (FAQs) Upgrading Keychain Security
Can hackers really copy my keys from a photo?
Yes. Visible keys can be cloned using just a smartphone photo. Keyport helps prevent this by storing your keys inside a housing that hides the blade fittings.
Are garage remotes vulnerable to hacking?
Yes. Many garage remotes use fixed codes that can be recorded and replayed. Even some newer remotes with rolling codes have been shown to be vulnerable to replay attacks. Leaving them visible - especially in your car - only increases your risk.
Does Keyport block RFID signals?
While Keyport isn’t a Faraday cage, carrying RFID fobs inside a metal-bodied organizer like the Pivot 2.0 can help reduce signal exposure. For extra security, consider pairing it with an RFID blocking sleeve or card.
Can I attach my car remote to my Keyport?
Yes. Keyport offers several attachment options, including the KO Magnetic Quick Release, which lets you detach your remote quickly and store it securely when not in use. You can also use a carabiner or lanyard loop, depending on your setup.
Is Keyport a good gift for security-conscious people?
Absolutely. It’s one of the best EDC gifts for dads, tech lovers, and gearheads who care about both function and discretion.